Published on: Aug 26, 2022
Advancements in technology often come at a cost. In this blog we’ll be discussing 5G RAN deployments and how they have become prone to security threats. Specifically we will be discussing how these issues arise in the cloud infrastructures that 5G networks leverage to cope with the increasing demand in network capacity as well as in the number of connected devices.
Cloud Infrastructures implement virtual networking in 5G that enables the dynamic allocation and management of networks for specific use cases, mobile network operators, or customers (see Fig. 1). Multitenancy in cloud infrastructure presents a significant security challenge, as the physical infrastructure is used and shared by multiple cloud infrastructure customers, e.g., mobile network operators. 
Fig. 1: 5G and Cloud computing [1]
Multitenancy emphasizes the importance of securely configuring technologies that isolate workloads (for example, virtualization/containerization) for each of those customers. Furthermore, cloud providers and mobile network operators may share security responsibilities in such a way that the operators must take responsibility for securing their “in the cloud” tenancy. Another factor posing security challenges is wireless carriers’ increasing use of a multi-cloud deployment model in 5G, with diverse and evolving architectures and design approaches.
To mitigate this danger, 5G cloud infrastructures must be created and configured securely, with capabilities to detect and respond to attacks, as well as a secure environment for implementing network operations.
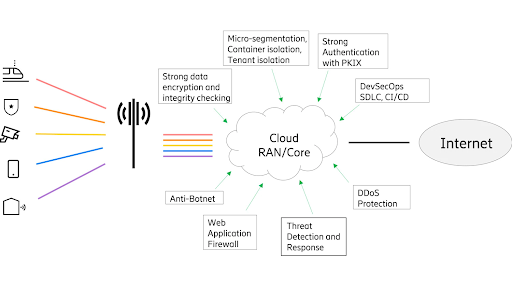
Fig. 2: Security controls for 5G Cloud RAN
The following secure practices needs to be addressed for security of 5G clouds (refer to Fig. 2):
- Detecting and preventing lateral movement: Identify malignant cyber actors within 5G clouds and prevent them from using a compromised cloud resource to compromise the entire network.
- Secure isolation of network resources: Ensure that virtual network functions are run in a secure environment with a focus on securing the container stack.
- Safeguard data during transit, use, and at rest: Ensure that customer and network data is protected at all times throughout the data lifecycle (while being stored, while being transmitted, and while being processed).
- Ensure the integrity of the infrastructure: Avoid unauthorized changes for 5G cloud resources.
Furthermore, a zero-trust architecture can be adopted, which is a security model built on the principle that no user, whether internal or external to the network and network functions can be trusted. In zero-trust architecture , there is no implicit trust granted to assets or users based on physical or network location, or ownership. This is related to cloud deployments that have multiple stakeholders: vendor, service provider, hyper-scale cloud provider, and system integrator.
Cloud RANs integrated with the above mentioned secure practices will incorporate the following security features:
- Creating a Hardware Root of Trust for Commercial Off-the-Shelf hardware with a Hardware Security Module .
- Establishing strong digital identities with digital signatures from a Certificate Authority.
- Use of 5G Authentication and Key Management, Extensible Authentication Protocol (Authentication and Key Agreement / Transport Layer Security) techniques for mutual authentication between device and network.
- Public-Key Infrastructure with strong cipher suites and Transport Layer Security or Datagram Transport Layer Security .
- Secure user access to containers of network components and cloud infrastructure with multi-factor authentication .
- For alerting and auditing, visibility, monitoring, and logging are required.
Moreover, Open RAN deployments should cater to the needs of data ownership whenever a public cloud is used. To ensure that data in transit, at-rest and in-use are protected, the service provider is responsible for establishing a multiparty relationship to agree upon clearly defined roles and responsibilities for protection against internal and external threats. Security control technologies and attack vectors need to be periodically assessed by all stakeholders.
To summarize, the security threat in Cloud 5G RAN can be reduced by adopting a zero-trust architecture that includes user multi-factor authentication and automated mutual authentication using PKI-based certificates. A secure cloud environment is constructed that includes secure hardware, micro-segmentation, threat detection and response, and user plane protection. An automated security management solution for policy configuration, access controls, configuration validation, logging, and run-time compliance monitoring, ensure the privacy of personal information and business-sensitive data, protect data-in-transit, data-at-rest, and data-in-use.
References:
[1] https://cloudcow.com/content/5-possible-ways-5g-will-impact-cloud-computing/#.YhszcOjMLIU
[2] https://www.ericsson.com/en/blog/2021/9/securing-cloud-ran-deployments





